
Born from the union between the English terms “farming” e “phishing”, More and more cybercriminal campaigns are using a new scam technique called pharming: the experts of Panda Security they explain to us what it is and how to protect ourselves.
Bank customers seem to be among the favorite victims and, more generally, users of platforms for exchanging and sending money. At the base of the campaigns is the goal of obtain personal data of victims, using manipulated IP addresses. In this way, users are unknowingly redirected to fraudulent websites.
What is pharming and how it works
As mentioned, pharming is an evolution of phishing, and as such aims to take unsuspecting victims to fraudulent sites to steal their information. Nevertheless, Unlike phishing, pharming does not necessarily require an error on the part of the victim.
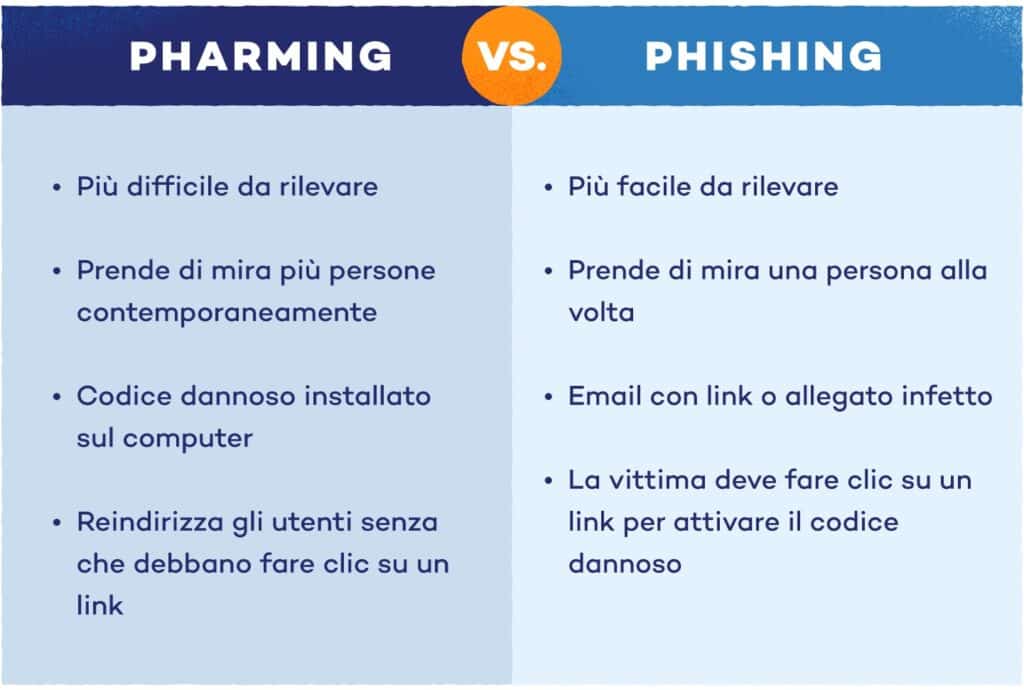
In fact, phishing tries to deceive victims through deceptive messages that convince them to click on links that refer to fraudulent sites or on infected attachments. In pharming, on the other hand, it is the cybercriminal who acts, hacking the victims’ computers or servers. Panda Security explains to us that the technique can take place in two ways:
- Hacking of individual computers– The hacker sends an email with a script that modifies the host files of the victim’s computer. Once the host files of the computer are infected, the victim is redirected to fraudulent web pages (IP different from the original one). Even if the user types the correct URL themselves, navigation is redirected because host files take priority over other elements on the system.
- Poisoning of DNS or DNS cache: The more radical version of pharming is that which directly targets DNS servers. These are public online servers that allow computers to connect to sites by translating the address entered by the user into the corresponding IP address. In this type of pharming, the hacker attacks the DNS server directly instead of hacking into a single computer. This type of attack is more difficult to land due to DNS security systems, but the ones that work have catastrophic consequences, affecting millions and millions of user URL requests.
How to tell if you are a victim of pharming
Panda Security explains that pharming attacks can be difficult to detect, especially if the fraudulent site is well made and difficult to distinguish from the original. However, there are some red flags such as:
- Minor changes to a link or site– Sometimes, hackers change some letters in the URL or use different graphics when creating the fraudulent site. If there are spelling errors, slightly different logo or with a lower resolution, different colors or that vary from page to page, beware: it could be a fraudulent copy of a pharming site.
- Unsecured connection: Many of the phishing and pharming pages continue to use URLs without a security certificate, so the address starts with “http” and not “https”. Some browsers or antivirus warn the user when the connection is not secure, but even in the absence of an explicit warning, if there is no lock icon to the left of the address, it could be a pharming site. All sites that manage sensitive data need a login and therefore a security certificate that protects the transmission of data over the Internet. A bank will never have an address that begins with HTTP only, without the final S.
- Unusual activity in the account or on the bank account: If you have suspicious movements in your bank account or unusual activity in your account, you could be the victim of a pharming attack.
- Unauthorized password changes: If a criminal manages to access a home banking account, he may try to change the password to prevent the owner from accessing. We recommend that you always enable security notifications and 2-factor authentication in your online accounts. This way you are notified whenever someone tries to change your credentials or log into your account.
- Unknown downloads and apps: If an app or program appears on your device that you don’t remember downloading. Periodically check the apps on your phone and computer and in case of suspicious app remove it immediately.
How to protect yourself from pharming attacks
Now that we understand what pharming is and how to recognize it, let’s understand how to protect yourself. However, Panda Security recommends following the following practices to be safer and mitigate the damage of a possible attack:
- If you think you are under attack, first thing clear the DNS cache
- It is recommended to download and keep constantly updated a good antivirus on all devices.
- In case of necessity contact the Internet service company.
- To browse safely, we recommend theuse of a VPN.














Leave a Reply
View Comments