
Intel applies a Tunable Replica Circuit to protect systems from certain types of fault injection physical attacks
Intel is an industry leader that creates technology that can change the world, making global progress possible and enriching people’s lives. The company presented a new technique that complements the mitigation measures of physical fault injection attacks already present at the software level. Fault injection protection uses hardware-based sensors to explicitly detect circuit timing malfunctions that occur following an attack. This is the first time that a TRC is offered in the family of Intel Core processors of the twelfth generation. The circuit adds fault injection detection technology to the Intel Converged Security and Management Engine. This is designed to detect non-invasive physical glitch attacks on the pins that supply clock and voltage. The TRC is also designed to detect electromagnetic fault injections.
Details on the new Intel: introduced the new Tunable Replica Circuit
Intel (here for more info) improves software reliability thanks to hardware improvements made using the logic present inside the processor. Today, the company presented a new technique that integrates the mitigation measures of physical fault injection attacks already present at the software level. Tunable Replica Circuit (TRC) represents protection against fault injection. It uses hardware-based sensors to explicitly detect circuit timing malfunctions that occur following an attack. As anticipated, the circuit adds the fault injection detection technology to the engine Intel Converged Security and Management Engine. It aims to detect non-invasive physical glitch attacks on the pins that provide clock and voltage in addition to electromagnetic fault injections.
Statements
The following are the first statements regarding the new Intel: introduced the new Tunable Replica Circuit.
Software protection is enforced with virtualization, canary stacks and code authentication before execution.
he has declared Daniel Nemiroff, Intel Senior Principal Engineer. Who then added:
This has prompted hackers to turn their attention to physical attacks on computer platforms. A favorite tool is fault injection attacks through voltage glitches, overclocks, and electromagnetic radiation. These cause circuit timing errors and can allow the execution of malicious instructions and the potential exfiltration of secret data.
The TRC was originally developed by Intel Labs to monitor dynamic variations such as voltage sags, temperature drops and aging in circuits. With the aim of improving performance and energy efficiency. As new technologies evolve, their applications also evolve.
By modifying the monitoring configuration and building the infrastructure to adjust the sensitivity of the TRC to fault injection attacks, the circuit has been optimized for security applications,
commented Charles Tokunaga, principal engineer of Intel Labs, explaining the research approach.
Collaboration
Intel Labs, iSTARE-PASCAL (Physical Attack and Side Channel Analysis Lab) e il Client Computing Group di Intel collaborated to test the TRC in different security scenarios. Together, the three actors demonstrated that the TRC can be calibrated to recognize such timing violations as the result of an attack. Intel applied the TRC as a hardware sensor to detect these fault injection attacks and protect systems.
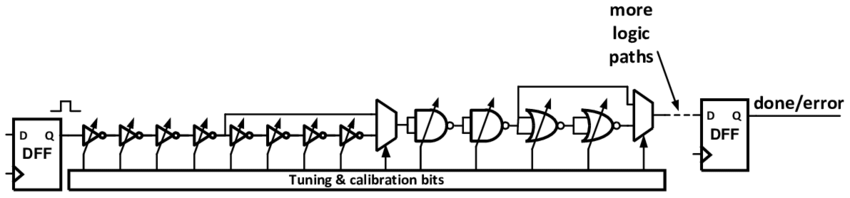
The purpose of the TRC
Il Intel’s TRC is designed to protect against certain types of physical attacks monitoring the delay of specific types of digital circuits. The TRC can signal an attack when it detects a timing error due to a voltage, clock, temperature, or electromagnetic failure. Because the TRC is calibrated to report errors that occur at voltage levels outside the CSME’s rated operating range, any reported error conditions indicate that data may be corrupted. This activates the appropriate mitigation operations to ensure data integrity.
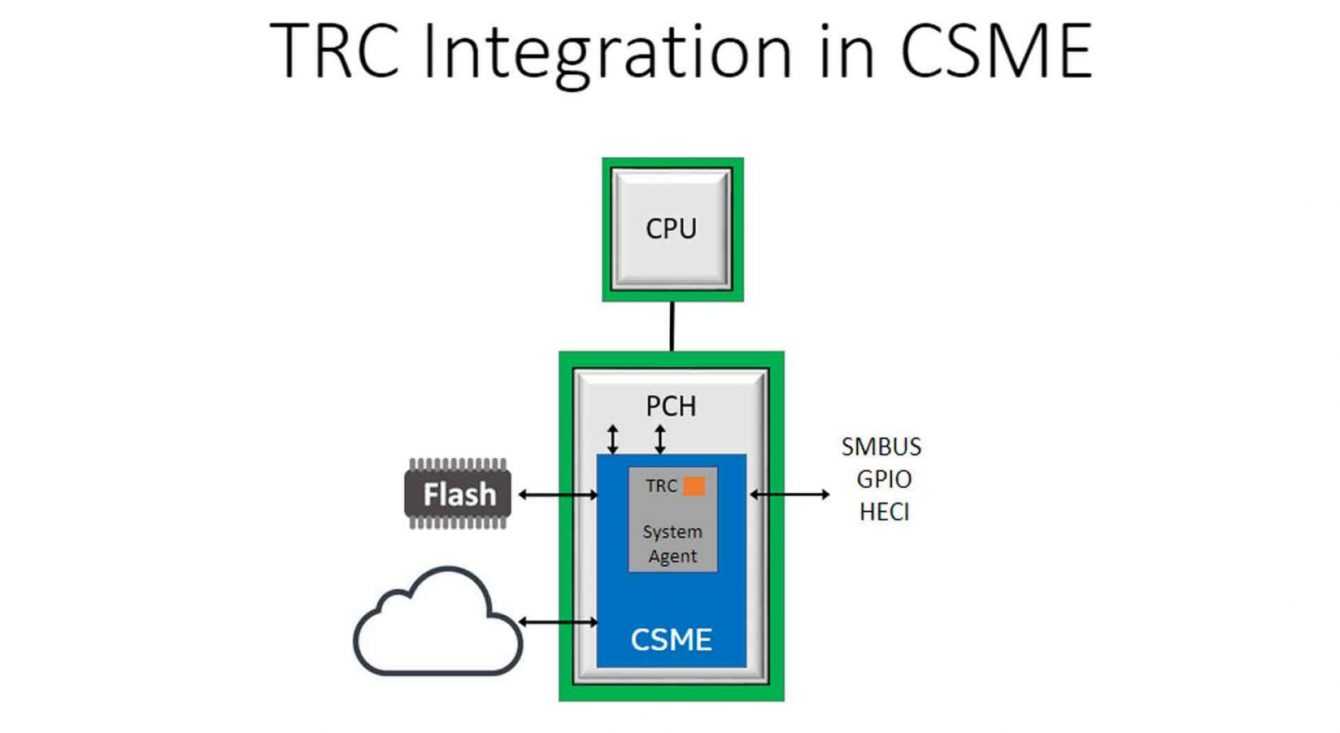
TRC al Platform Controller Hub
Intel has applied the TRC al Platform Controller Hub (PCH), a separate chipset, isolated from the CPU, which improves the Root of Trust protection of a system, called Intel CSME. The most important aspect of manufacturing this type of hardware sensor is calibration. Calibrated with too high a sensitivity, the sensor would detect normal workload voltage drops as false positives. False positives disrupt error detection and could cause platform instability, placing an additional burden on cybersecurity managers. To avoid false positives, Intel has developed a feedback-based calibration flow. Minimizing false negatives is also important, so the feedback loop uses false positive and false negative test results, along with hardware sensor margin data. This indicates how close the sensor is to detecting a glitch and the accuracy of the protection bands.
Architectural progress
Architectural advancements often result in significantly lower execution benefits than software-only implementations. However, physical attacks have always been overlooked among the threat models. As computing power grows at the intelligent edge, Intel invests in physical attack protection features. This is to improve the resilience of software that operates with increasingly high workloads and constantly evolving threats. Security is a system-level property rooted in silicon. Every component of the system, from software to silicon, can help protect data. Details of this research were presented at Black Hat USA 2022: Fault-Injection Detection Circuits: Design, Calibration, Validation and Tuning.
And you? What do you think of the new Tunable Replica Circuit di Intel ? Let us know with a comment and stay tuned to TechGameWorld.com for more news and reviews from the world of technology (and more!).
The Intel article: introduced the new Tunable Replica Circuit comes from TechGameWorld.com.















Leave a Reply
View Comments