In this article we will explain what a cryptolocker ransomware is but above all how to prevent this type of threat using new generation tools
Today there is (too much) talk of the “ChatGPT risk” and too little of a much more serious threat: the CryptoLocker ransomware. While the former is an unproven danger, CryptoLocker ransomware is a real problem that costs real money. And many.
In Italy, the average ransom is $709,746. If we also count the costs of interruption of service, we reach dizzying figures: 5,600 dollars a minute reports Gartner – not to mention the hefty fines and damage to reputation. It is a business that knows no crisis, with a growth rate of 500% a year.
A real pandemic. In which, sadly, we are on the podium: Italy is first in Europe for ransomware attacks — worse than us only USA, Japan, Turkey, India, Taiwan and Mexico. That’s why if in the distant past it might have made sense to cross your fingers, today luck is no longer enough.
Gartner estimates that 75% of companies will experience a ransomware attack within two years. What does it mean? That you have a 75% chance of paying the aforementioned ransom money. Translated: by 2025 you will have to pay out 531 thousand euros. If everything goes well! Remember that we are talking about the average ransom. If luck isn’t on your side, you could find yourself paying a lot more. That’s why you have to right away run for cover.
What is CryptoLocker ransomware: if you know it, you avoid it
CryptoLocker ransomware is the first ransomware of the modern era. Appearing on the internet in 2013, it immediately reached global diffusion thanks to bitcoin, which the malware used (and still uses) to collect the ransom payment.
But CryptoLocker is not malware like any other. It’s a trojan that infects your computer and searches your hard drive, peripherals, everything for files. And not only that: it also searches your cloud space. Once files are found, CryptoLocker ransomware encrypts them with an RSA-2048-bit asymmetric key, which a conventional computer can decrypt in 300 trillion years. Simply put, it’s impossible.
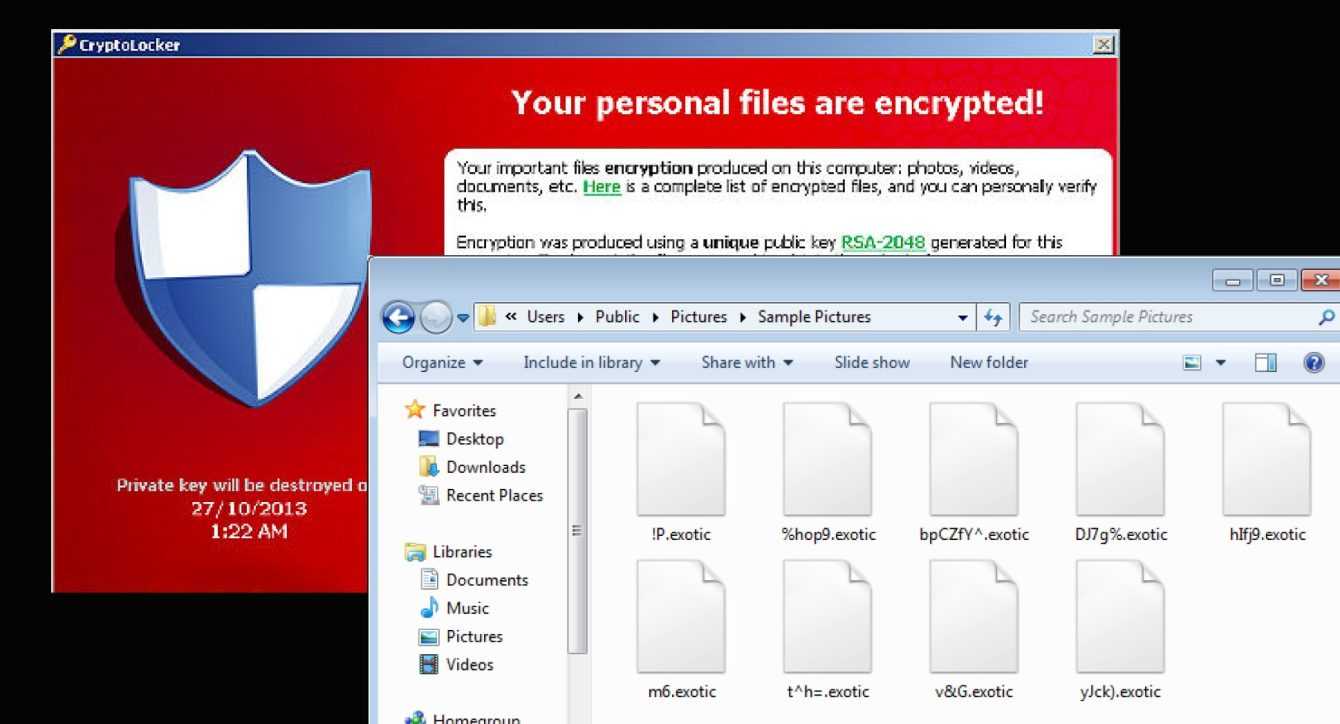
Is there anything left but to pay? Absolutely not. On the contrary: experts advise against paying — not only because this fuels cybercrime, but also (and above all) because there is no guarantee that paying will do anything. According to the Sophos State of Ransomware 2022 report, over half of victims pay the ransom, but only a quarter have all of their data returned. So what to do if you are a victim of CryptoLocker ransomware?
CryptoLocker Ransomware: Survival Guide
As you may have read everywhere, the number 1 method to prevent a ransomware attack is to have a backup. However, this does not mean that you can restore your backup as if nothing had happened! On the contrary, you have to pay close attention to ed avoid restoring your backups to the same machine that was infected with the ransomware. It is likely that the ransomware was designed in such a way that it encrypts files once it is restored — which is why it is essential to first delete the malware and only then restore everything. Or alternatively, restore to an uninfected machine.
The first step is therefore to isolate the virus and identify it: according to the European Cybercrime Center in fact CryptoLocker is often used by the media as a generic term to mean different ransomware. There are many types of ransomware and cybercriminals are constantly developing new variants of them, so you will need to rely on an analysis tool — there are many on the web (even free ones) that can determine the type of ransomware by examining a single encrypted file or even simply by comparing the ransom note with those commonly used on the net. Some common types of ransomware include BadRabbit, BitPaymer, Cerber, SamSam, and WannaCry, which was the star of a global attack on Windows computers in May 2017.
What if I don’t have a backup?
At this point you may be wondering: what if I don’t have a backup? Is there a kind of “tow truck” to call when you have a puncture and you don’t have a spare wheel? In other words: is there any chance of recovering the data or do you really need to put your mind at peace? Don’t despair: all is not lost if you know how to restore files encrypted by ransomware (for free) even without a backup.
Once you find out what ransomware it is, you can try to decrypt it. Wasn’t decrypting the files without the key impossible? Yes… if the ransomware is done right. But there are no longer the hackers of the past: today many would-be cybercriminals buy real ransomware packages on the dark web — the so-called ransomware as a service, or RaaS.
As some of the ransomware makers are finding out, creating a program that encrypts efficiently is quite difficult. Some of these ransomware are so poorly written that an expert who knows how to interpret the code can find a way to decrypt files without knowing the password. In some cases, even the decryption key can be found in the code itself.
It must be pointed out, however, relying on this eventuality is not a strategy, but rather the last resort in case you have not taken the right precautions. If you want to be prepared, theonly solution is to prevent the attack first.
How to prevent a ransomware attack
According to the FBI, phishing is the top attack vector for ransomware. Verizon’s 2022 report estimates that 36% of all data breaches begin with phishing — an average of one ransomware attack every eleven seconds. If you haven’t figured it out yet, the first thing to keep in mind when it comes to protection against ransomware attacks is to protect yourself from phishing.
But what is phishing, exactly? Phishing is a form of cyberattack in which an attacker tries to obtain sensitive information, such as passwords or bank details, by posing as a trusted entity, such as a bank or company that the user is dealing with. Usually, phishing happens via email, but it can also happen via text messages or social media.
How can you protect yourself from phishing? Here are some useful tips:
- Be careful with the emails you receive. Do not click on suspicious links or download attachments from unverified sources. If an email seems suspicious, check the sender’s address and look for any spelling or grammar errors.
- Never give personal or sensitive information to untrustworthy people or websites. Remember that banks and other reputable entities never ask for passwords or bank details in emails or messages.
- Use up-to-date and reliable security software, such as antivirus and firewalls, and always keep them updated.
- Pay attention to your login credentials and change your passwords regularly. Use strong and unique passwords for each account.
- If in doubt, contact the relevant company or agency directly via their official website or published phone numbers, rather than replying to a suspicious email or message.
Remember that phishing is just one of the many ways ransomware can penetrate computer systems. By following these precautions, you can greatly reduce the risk of falling victim to a phishing attack and consequently a ransomware attack. However, keep in mind that if you are looking for a truly definitive solution, nothing beats an immutable backup.
An immutable backup a day keeps ransomware away
An immutable backup is a backup in which the archived data cannot be changed or deleted for a certain period of time set by the user. This type of backup is usually created through the use of an S3 compatible object storage, such as AWS, Azure or the Italian Cubbit.
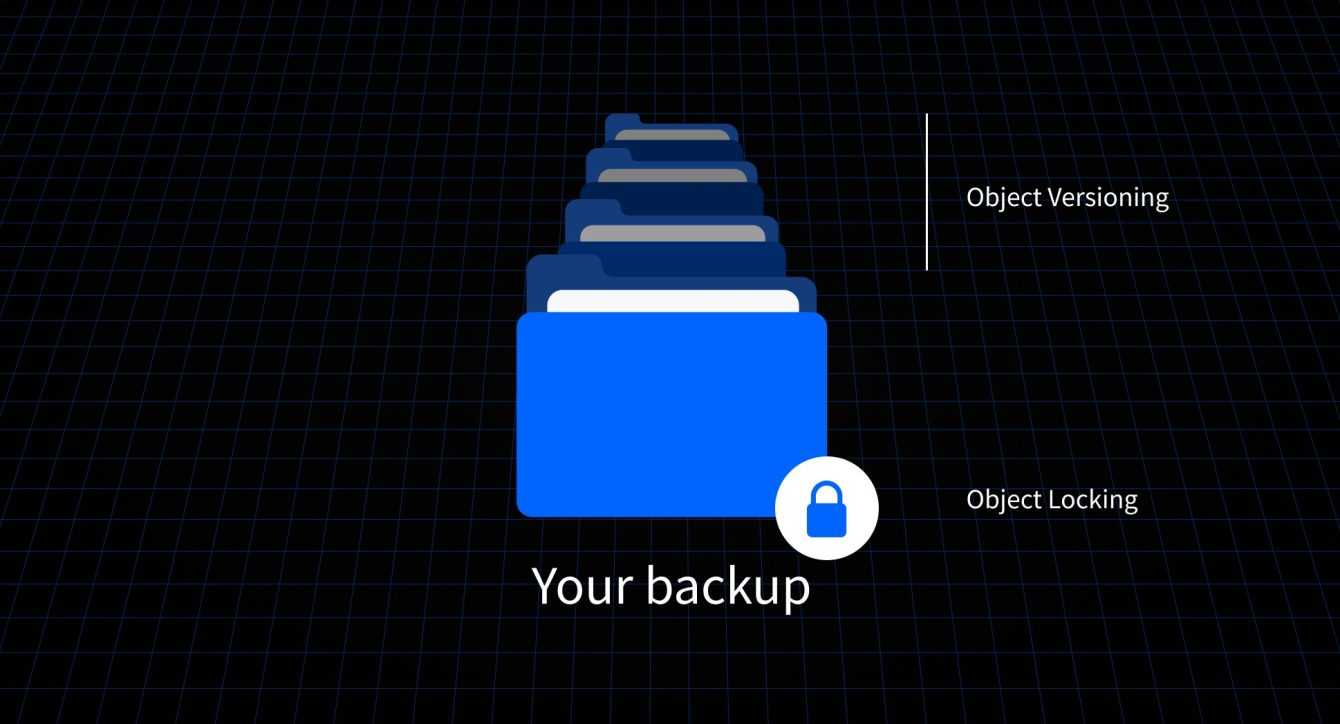
Without going into too much detail on what object storage is, it’s a next-generation data storage model that protects you from ransomware thanks to two innovative features:
The function of S3 Object Locking lets you lock down objects stored in an object storage bucket from being deleted or modified for a specified amount of time (a bucket, if you’re wondering, is simply a container of objects). This means that if a ransomware tries to encrypt or delete your data, it will not be able to do so since the objects are protected by the lock. This allows you to easily restore data in the event of a ransomware attack, without having to pay the ransom.
The function of S3 Object Versioning instead it allows you to keep different versions of the objects stored in one bucket. Whenever an object is modified or deleted, a new version is created, which can be recovered at any time. Which means: if a ransomware deletes or encrypts an object, you can easily restore the previous version, avoiding losing important data.
Why choose Cubbit, the ultimate anti CryptoLocker solution
Cubbit is an innovative cloud object storage that costs 80% less than AWS, but above all it is a next-generation solution for data recovery from ransomware. Unlike other object storage, it is geo-distributed. Instead of saving your data in a data center, in fact, Cubbit encrypts them with AES-256, divides them into parts and distributes them in a peer-to-peer network of energy-efficient devices under the control of the user companies (Amadori, Granarolo and over 100 companies are already using it). This guarantees maximum security and risk diversification by design
Cubbit is S3 compatible and supports S3 Object Locking, S3 Object Versioning and S3 Multipart Upload. The user interface is really simple and, if that wasn’t enough, there’s a step-by-step guide for making a backup whatever your S3 stack (Veeam, QNAP, Synology, etc).
Would you like to know more? In this video, Cubbit’s IT specialists create CryptoLocker ransomware and simulate a real attack on files and folders. After that, they show how to retrieve data using the object storage features mentioned above.
If you want to test Cubbit’s geo-distributed object storage for yourself, you can try it for free today from the official site.
















Leave a Reply
View Comments