Thousands of users have downloaded the app spy FlyGram e Signal Plus Messenger from Google Play Store and Samsung Galaxy Store. These are two active campaigns aimed at Android users of Telegram and Signalwho spread it spyware BadBazaar attributable to the China-aligned APT GREF group.
Spyware BadBazaar nelle app Telegram e Signal
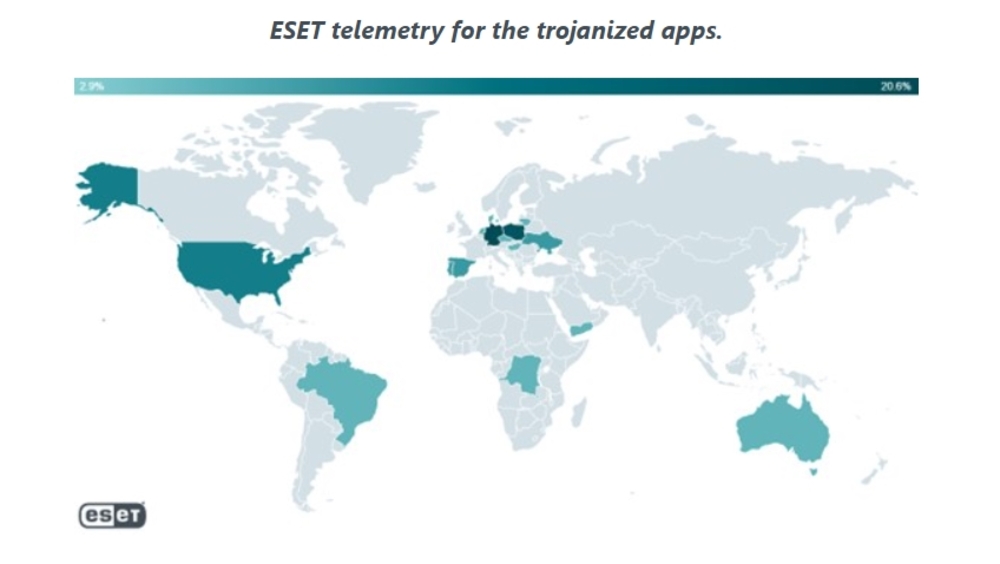
The leading group in cybersecurity ESET identified two threats from the Chinese group GREF aimed at Android users. Probably active since July 2020 for Signal and July 2022 for Telegram, the two campaigns distributed the BadBazaar spy code. Diffusion happens via Google Play Store, Samsung Galaxy Store and dedicated websitesposing as legitimate encrypted chat applications.
The two offending apps are FlyGram e Signal Plus Messenger, downloaded by thousands of users in Europe and the United States. But ESET has also reported detections in Ukraine and other countries around the world. Subsequently, both apps were removed from Google Play.
“BadBazaar’s malicious code was hidden in Trojan-affected apps from Signal and Telegram, which provide victims with a working app experience, but with spying activity in the background,” he explains Lukáš Štefanko, ESET researcher who made the discovery. “The main purpose of BadBazaar is to exfiltrate your device information, contact list, call logs and installed apps list, and to conduct spying on Signal messages by secretly connecting the Signal Plus Messenger app of the victim to the attacker’s device.”
In particular, FlyGram – the fake Telegram app – can access Telegram backups if the user has activated a special function inserted by the attackers. This spyware feature was activated by at least 13,953 user accounts.
You can follow all available updates on GREF spyware campaigns regarding BadBazaar and other apps on the official ESET WeLiveSecurity website.















Leave a Reply
View Comments