The hacker they are targeting the refugee crisis in Ukraine e they try to boycott fundraisers. Several cyberattacks have in fact hit the major organizations they are trying to helping refugees flee Ukraine.
According to sources, some of these hackers may be linked to the Belarus. It also appears that the attackers have access to the email account of at least one Ukrainian military officeraccording to American cybersecurity researchers.
Hackers and refugees in Ukraine: cyberattacks on organizations
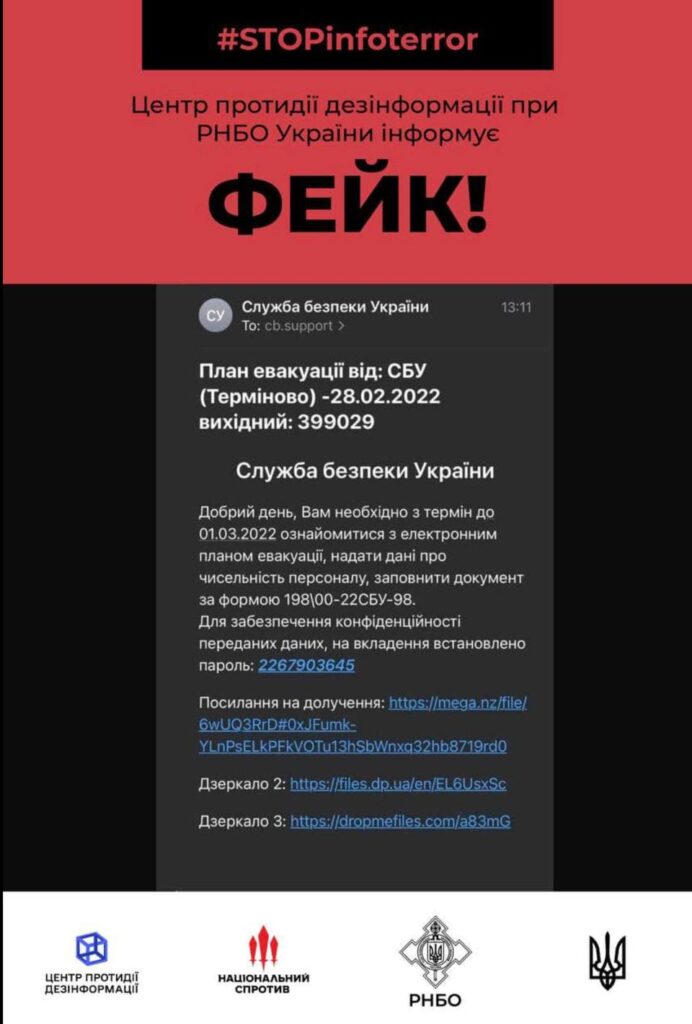
Earlier this week, numerous phishing attacks hit various targets across Ukraine. The hackers pretended to offer information on evacuation plans from the country. The Ukrainian government then warned its citizens, stating that it was a fake. Additionally she reported that the documents contained within the emails were malware.
Forbes got it screenshot (which you can see above) from one of the phishing emails, sent to a Gmail account. Google then stated that “similar messages are used to steal people’s personal information”. The messages spoke of evacuation plansaccording to the SBU, and contained a letter attached (malware).
Researchers from the internet security company ESETbased in Slovakia, told Forbes it was software-based malware Remote Utilities di Microsoft for Windows. This malware, as revealed, allows theexternal access to computers. “The sample is fresh but the malware itself is not that sophisticated,” an ESET spokesperson said.
Wednesday, researchers from the US cybersecurity company Proofpoint have confirmedato several phishing attacks “Evacuation theme”. These attacks targeted a Unnamed European government agency. Proofpoint security researchers looked at emails sent from an address ending with @ukr[.]neta “possible compromised email account of a member of the Ukrainian armed service”.
The attacks continue
The emails targeted “European government personnel involved in managing the logistics of refugees fleeing Ukraine. Here the email used the subject IN COMPLIANCE WITH THE DECISION OF THE EMERGENCY MEETING OF THE SECURITY COUNCIL OF UKRAINE DATED 24.02.2022. ”
One spreadsheet inside the email contained malware known as SunSeed. SunSeed’s function is to act as a path on an infected PCpermitting installing more malwareProofpoint said. The team stated:
There was a clear preference. Hackers have targeted individuals with responsibilities related to transportation, financial and budget allocation, administration and movement of the population in Europe. This campaign may represent an attempt to gain insight into the logistics surrounding the movement of funds, supplies and people within NATO member countries.
The ability to exploit intelligence around refugee movements in Europe for disinformation purposes is a proven part of Russian and Belarusian state techniques.
Catherine WoolardDirector of the European Council for Refugees and Exiles, told Forbes they have been there more phishing messages than usual about the community. “We are hearing this from across the industry and from related entities, political foundations, for example,” he added. “We are used to being a low-level target for various actors, and many of our members have fairly extensive confidence. Usually in response to the surveillance of their governments, though. ”.
A link with Belarus?
The researchers “tentatively” attributed the attacks to a group widely known as UNC1151linked by other cybersecurity researchers to the Belarusian government. They said that while there were no obvious technical links, the behavior and the timing of the attacks indicated UNC1151, also known as Ghostwriter.
Proofpoint’s analysis came after the Computer Emergency Response Team of the Ukrainian government said that “mass phishing emails targeted the private ‘i.ua’ and ‘meta.ua’ accounts of Ukrainian military personnel and related individuals”. The goal was to take control of email accounts. Later the hackers would use the contact details from the victim’s address book to send more phishing emails.
CERT blamed UNC1151, claiming that its members were “officers of the Ministry of Defense of the Republic of Belarus”. The cybersecurity society Mandiant he then attributed the attacks to group linked to Belarus.
Both Google and Facebook said they saw hackers “target the Ukrainian government and military officials. We have blocked these attempts and have not seen any compromise of Google accounts as a result of this campaign ”.
Meanwhile, ESET released a report on Tuesday. In the aforementioned report he indicates that cyberattacks designed to wipe out the computers of the Ukrainian government and companies have been launched a few hours before the start of the land invasion.
The malware was created in the month of October 2021, it therefore appears that “the attacks had been planned for several months,” the company said. At the same time, the Ukrainian targets were hit with a ransomware “bait” to distract from destruction of computer memory.















Leave a Reply
View Comments