A group of researchers has discovered a app group, downloaded from Play Store about 300,000 times, who later turned out to be gods trojan bancari. The aforementioned applications, apparently harmless, they actually stole banking credentials from users and logged keystrokes. Let’s find out all the details.
Play Store: These apps were downloaded 300,000 times but were banking Trojans
The apps – which present themselves as scanner QR, scanner PDF e cryptocurrency wallets – belonged to four separate families of Android malware spread over the course of four months. The bad guys have used several tricks to bypass the restrictions that Google has come up with in an effort to curb the relentless distribution of fraudulent apps in its official marketplace.
“What makes these Google Play distribution campaigns very difficult to detect from an automation (sandbox) and machine learning perspective is that the dropper apps all have a very small malicious footprint,” the researchers wrote in a post. mobile security company ThreatFabric. “This small footprint is a (direct) consequence of the authorization restrictions applied by Google Play.”
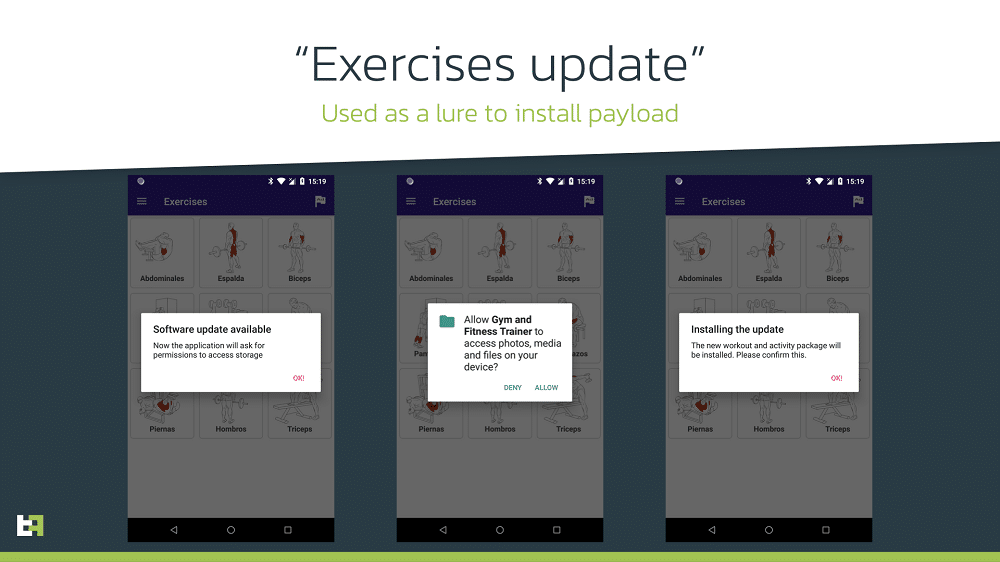
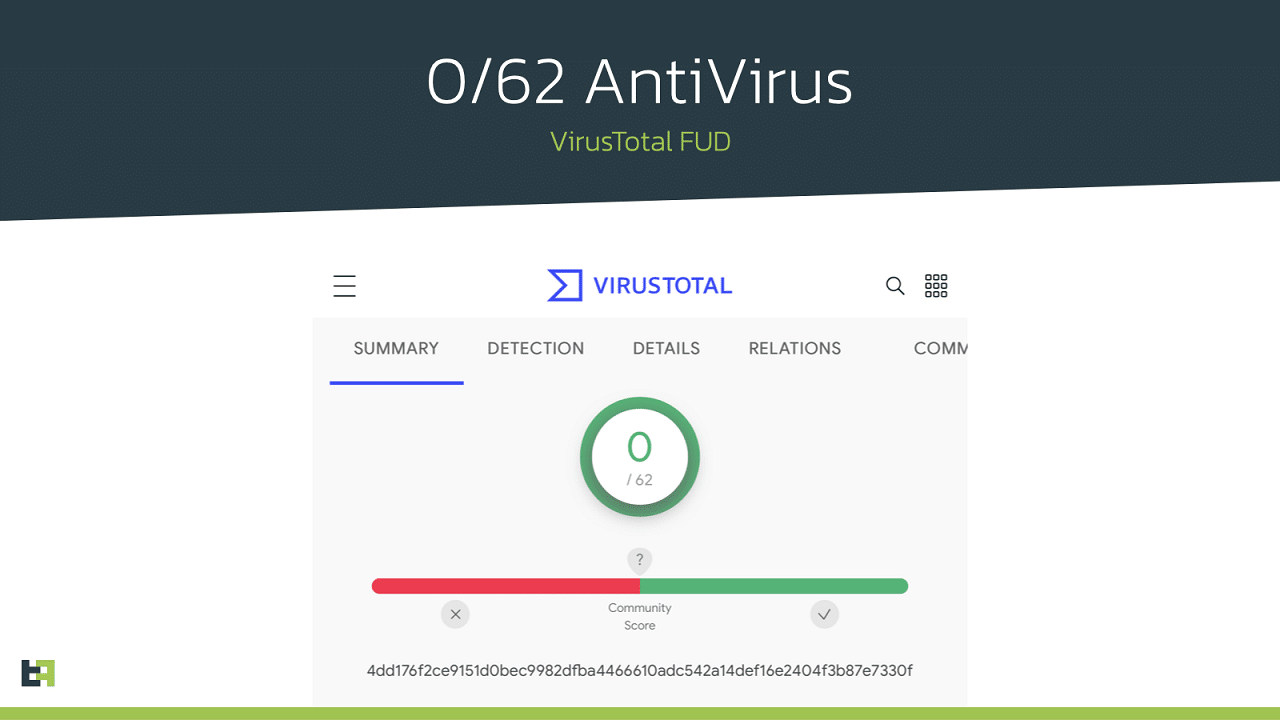
Here’s what it means. The campaigns initially delivered a harmless app. After the app was installed, users received messages prompting them to download updates with additional functions. Apps often required updates to be downloaded from third party sources but at that point, many users trusted without problems. Most apps initially had zero detections by the malware checkers available on VirusTotal.
Moreover, in many cases, malware operators they installed manually malicious updates only after having checked the geographic location of the infected phone.
The most dangerous malware
The malware family responsible for the most infections is known as Anatsa. This “pretty advanced Android banking trojan” offers a variety of capabilities, including remote access e automatic transfer systems, that they empty automatically victims’ accounts and send the content to accounts belonging to the malware operators.
The researchers wrote:
The process of infection with Anatsa looks like this: at the beginning of the installation from Google Play, the user is forced to update the app to continue using it. At this moment, Anatsa’s payload is downloaded from the C2 server and installed on the unsuspecting victim’s device.
The actors behind it took pains to make theirs look like legitimate and useful apps. There are a large number of positive reviews for the apps. The number of installations and the presence of reviews can convince android users to install the app. Furthermore, these apps actually possess the claimed functionality; after installation, they function normally and further convince the victim of their legitimacy.
Despite the overwhelming number of installations, not all devices that have installed these droppers will receive Anatsa, as the bad guys have made efforts only to target the regions of their interest.
Finally, the researchers found three other malware families: Alien, Hydra ed Ermac. One of the droppers used to download and install malicious payloads was known as Gymdrop. It used filter rules based on the infected device model to prevent targeting of search devices.
The guilty apps
| Two Factor Authenticator | com.flowdivison | a3bd136f14cc38d6647020b2632bc35f21fc643c0d3741caaf92f48df0fc6997 |
| Protection Guard | com.protectionguard.app | d3dc4e22611ed20d700b6dd292ffddbc595c42453f18879f2ae4693a4d4d925a |
| QR CreatorScanner | com.ready.qrscanner.mix | ed537f8686824595cb3ae45f0e659437b3ae96c0a04203482d80a3e51dd915ab |
| Master Scanner Live | com.multifuction.combine.qr | 7aa60296b771bdf6f2b52ad62ffd2176dc66cb38b4e6d2b658496a6754650ad4 |
| QR Scanner 2021 | com.qr.code.generate | 2db34aa26b1ca5b3619a0cf26d166ae9e85a98babf1bc41f784389ccc6f54afb |
| QR Scanner | com.qr.barqr.scangen | d4e9a95719e4b4748dba1338fdc5e4c7622b029bbcd9aac8a1caec30b5508db4 |
| PDF Document Scanner – Scan to PDF | com.xaviermuches.docscannerpro2 | 2080061fe7f219fa0ed6e4c765a12a5bc2075d18482fa8cf27f7a090deca54c5 |
| PDF Document Scanner | com.docscanverifier.mobile | 974eb933d687a9dd3539b97821a6a777a8e5b4d65e1f32092d5ae30991d4b544 |
| PDF Document Scanner Free | com.doscanner.mobile | 16c3123574523a3f1fb24bbe6748e957afff21bef0e05cdb3b3e601a753b8f9d |
| CryptoTracker | cryptolistapp.app.com.cryptotracker | 1aafe8407e52dc4a27ea800577d0eae3d389cb61af54e0d69b89639115d5273c |
| Gym and Fitness Trainer | com.gym.trainer.games | 30ee6f4ea71958c2b8d3c98a73408979f8179159acccc01b6fd53ccb20579b6b |
| Gym and Fitness Trainer | com.gym.trainer.games | b3c408eafe73cad0bb989135169a8314aae656357501683678eff9be9bcc618f |














Leave a Reply
View Comments