The experts of Check Point Research (CPR) reveal new activities and hacker attacks against Russia and its state defense institutes. It would be a cyber-espionage campaign operated by several Chinese APT groups. They are allegedly attempting to exploit the numerous Western sanctions against the Kremlin as a bait business for espionage operations. Moreover, the sanctions have brought particular pressure on the Russian economy, especially on the industrial sector.
The research shows that these campaigns are actually part of a broader spying framework by Chinese hackers, who have been targeting various organizations linked to Russia for some months now. The report prepared by CPR also reveals the functioning of the baiting methodologies, which generally come in the form of phishing campaigns, often very elaborate.
Spear-Phishing: inside the hacker attacks against Russia
Check Point Research offers us an example of spear-phishing used in these campaigns. These are obviously attacks that can take various forms (from SMS to social media), even if the preferred means of cyber-spies seems to remain e-mail. The CPR report reads:
On March 23, malicious emails targeted several Russian-based defense research institutes. The e-mails, which had as the subject “List of
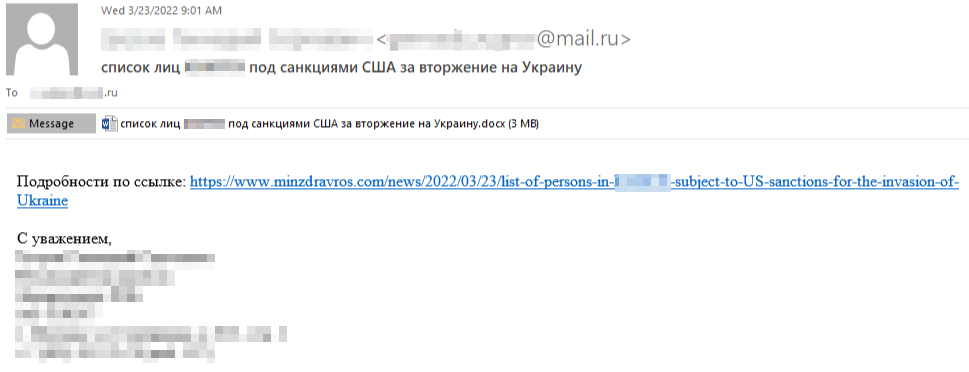
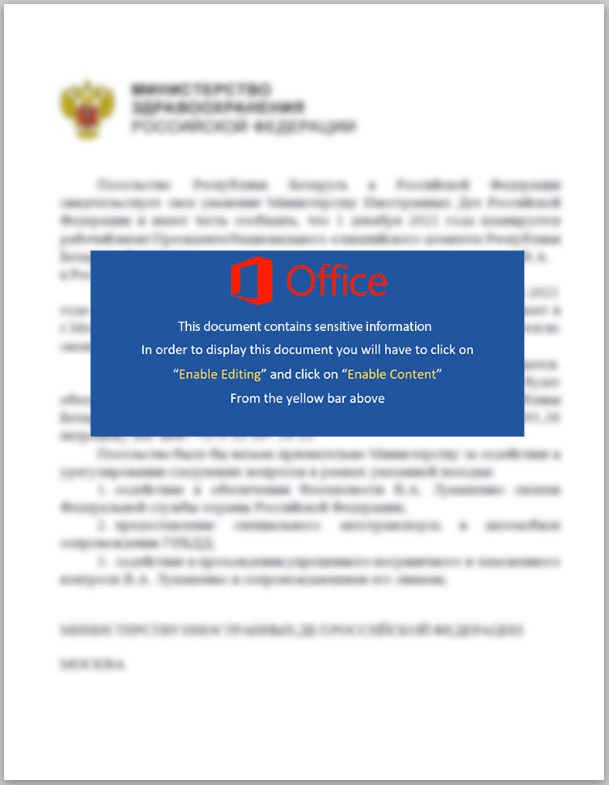
The email contained a series of attached documents, all made in an absolutely credible way, so much so that they appeared to be official documents of the Russian Ministry of Health, complete with coat of arms and official title:
On the same day, another very similar phishing email arrived to an undisclosed entity in Minsk, Belarus, with the subject “US Spread of Deadly Pathogens in Belarus”.
Is China behind all this? The word to the CPR experts
The researchers considered the methodologies and procedures used (TTP), coming to the conclusion that it is a Chinese hacker APT, without identifying the specific culprit. The report reads:
“Chinese groups are known for reusing and sharing tools. The Twisted Panda campaign bears multiple similarities to advanced and long-standing Chinese cyber-espionage hackers, such as the obfuscation of control flows observed in SPINNER which was previously used by the Chinese group APT10 and reappeared in a recent campaign named Mustang Panda. . However, there is not strong enough evidence, such as connections located in infrastructure, to point the finger at a specific Chinese group ”.
The research also mentions the Made in China 2025 plan. This consists of a roadmap that will lead China to become a world leader in several key sectors (such as robotics and healthcare equipment).
CPR finally reveals that the Russian research institutes attacked belong to a holding company of the Russian state defense conglomerate Rostec Corporation. The latter is the largest Russian holding company in the radioelectronics sector. The research institutes targeted are primarily concerned with the development and production of electronic warfare systems, military on-board radio electronic equipment, airborne radar stations and state identification means.
At this link you can consult the complete report drawn up by Check Point Research.
















Leave a Reply
View Comments