HP Inc. today released its latest Global Threat Insights Report, which provides an analysis of cybersecurity attacks and vulnerabilities in the real world. Research shows a increase significant of the frequency and of sophistication of the activity of cybercrime, including a 65% increase in the use of hacking downloaded from underground forums e Web sites in file sharing from the second half of 2020 to the first half of 2021. To get these reports ready, HP created HP Wolf Security, a cyber attack protection system.
The researchers noted that the instruments hacking was widespread surprisingly capable. For example, a tool can solve CAPTCHA challenges using computer vision techniques, namely optical character recognition (OCR), in order to perform credential-filling attacks against websites. More generally, the report found that cybercrime is more organized than ever, with underground forums that provide a perfect platform for threat actors to collaborate and share attack tactics, techniques and procedures.
“The proliferation of pirate hacking tools and underground forums allows previously low-level actors to pose serious corporate security risks,” says Dr. Ian Pratt, Global Head of Security, Personal Systems, HP Inc. “At the same time, users continue to fall prey to simple phishing attacks over and over again. Security solutions that arm IT departments to keep pace with future threats are critical to maximizing business protection and resilience“.
The most common criminal cyberattacks:
- Collaboration between cybercriminals is opening the door to larger attacks on victims: the affiliates of Dridex they are selling access to hacked organizations to other threat actors so they can distribute ransomware. The decline in the activity of Emotet in the first quarter of 2021 resulted Dridex to become the leading malware family for cyber attacks isolated from HP Wolf Security.
- Information thieves delivering more malicious malware: malware CryptBot, historically used as an infostealer to steal credentials from cryptocurrency wallets and web browser, is also used to deliver DanaBot, a banking trojan run by organized crime groups.
- VBS downloader campaign aimed at business executives: a campaign Visual Basic Script Multi-stage (VBS) shares malicious ZIP attachments named after the executive it targets. Deploy a stealthy VBS downloader before using legitimate SysAdmin tools to “live the earth”, persist on devices, and deliver malware.
- From application to infiltration: A resume-themed malicious spam campaign targeted shipping, shipping, logistics and related companies in seven countries (Chile, Japan, UK, Pakistan, US, Italy and Philippines), leveraging a Microsoft Office vulnerabilities to distribute commercially available Remcos RAT and gain backdoor access to infected computers.
HP Wolf Security, HP’s answer to cyberattacks
The results are based on data from HP Wolf Security, which tracks cyber attacks and malware within isolated micro-virtual machines to understand and capture an entire chain of infections and help mitigate threats. By better understanding the behavior of the malware in nature, researchers and engineers of HP Wolf Security I am able to rstrengthen the protections endpoint security e resilience overall system in view of further cyber attacks.
“The cybercrime ecosystem continues to develop and transform, with more opportunities for petty cybercriminals to connect with larger actors within organized crime and download advanced tools that can bypass defenses and breach systems,” he notes Alex Holland, Senior Malware Analyst, HP Inc. ”We are seeing hackers adapt their techniques to promote greater monetization by selling access to organized criminal groups so they can launch more sophisticated attacks against organizations. Malware strains such as CryptBot previously would have been a danger to users using their PCs to store cryptocurrency wallets, but now they also pose a threat to businesses. We see infostealers distributing malware run by organized criminal groups, which tend to favor ransomware to monetize their access “.
Other key findings from the report include:
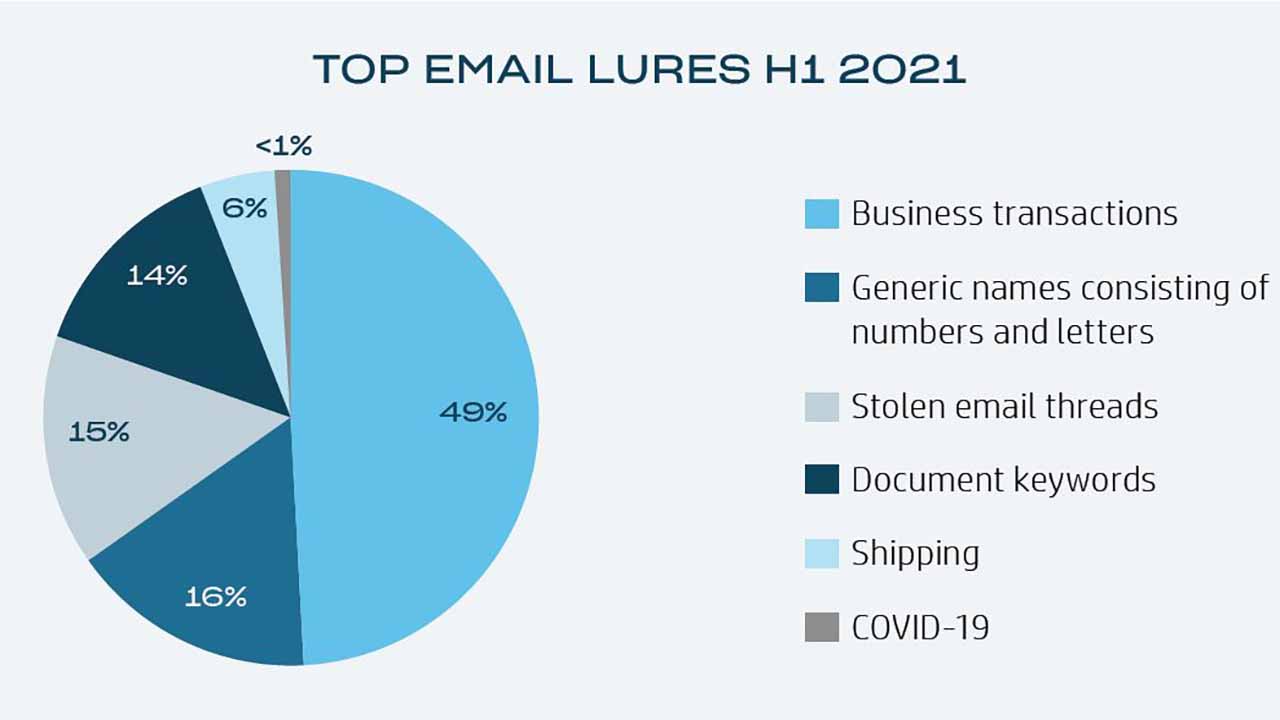
- 75% of the malware detected was sent by email, while i download from the web they were responsible for the remaining 25%. Threats downloaded using web browsers increased by 24%, partially driven by users downloading hacking tools and cryptocurrency mining software. The phishing lures more common were invoices and business transactions (49%), while 15% were replies to intercepted email threads. Phishing lures mentioning COVID-19 made up less than 1%, down 77% from the second half of 2020 to the first half of 2021.
- The most common type of malicious attachments they were archive file (29%), spreadsheets (23%), papers (19%) and executable files (19%). Unusual archive file types, such as JAR (Java archive files), are used to avoid detection and scanning tools and install malware readily available in underground markets.
- The report found that the 34% of the malware caught was unknown previously, a decline of 4% compared to the second half of 2020
- An increase in the 24% of malware exploiting CVE-2017-11882, a memory corruption vulnerability commonly used to exploit Microsoft Office or Microsoft WordPad and perform fileless attacks.
“Cybercriminals are easily bypassing detection tools by simply tweaking their techniques. We have seen a wave of malware distributed via uncommon file types such as JAR files, which are probably used to reduce the chances of being detected by anti-malware scanners, ”he comments Holland. “The same old phishing tricks are luring victims, with transactional-themed baits convincing users to click on malicious attachments, links and web pages.”
“As cybercrime becomes more organized and smaller players can easily obtain effective tools and monetize attacks by selling on access, there is no such thing as a minor breach,” he concludes. Pratt. “The endpoint continues to be a huge target for cybercriminals. Their techniques are becoming more sophisticated, so it is more important than ever to have a complete and resilient endpoint infrastructure and cyber defense. This means using features such as threat containment to defend against modern attackers, minimizing the attack surface by eliminating threats from the most common attack vectors: email, browser and downloads. “














Leave a Reply
View Comments