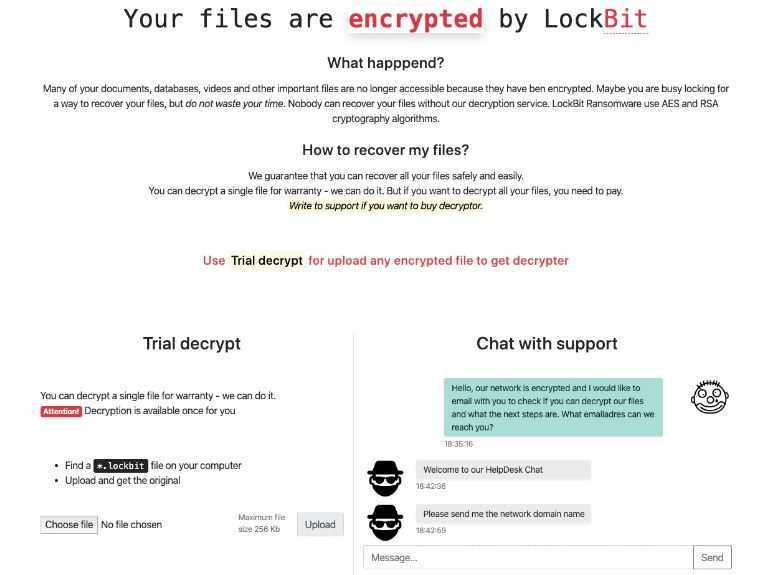
Detected for the first time in September 2019, LockBit is a ransomware that the authors have modified over time, making it increasingly sophisticated and unique.
LockBit is part of a sub-class of the ransomware family known as “cryptographic virus“. Normally a ransomware encrypts the victim’s data, demanding a ransom in order to get it back; LockBit in addition to performing the classic ransom request procedure, threatens the victim to spread the data in the clear on the internet, in the event that the requested ransom is not paid.
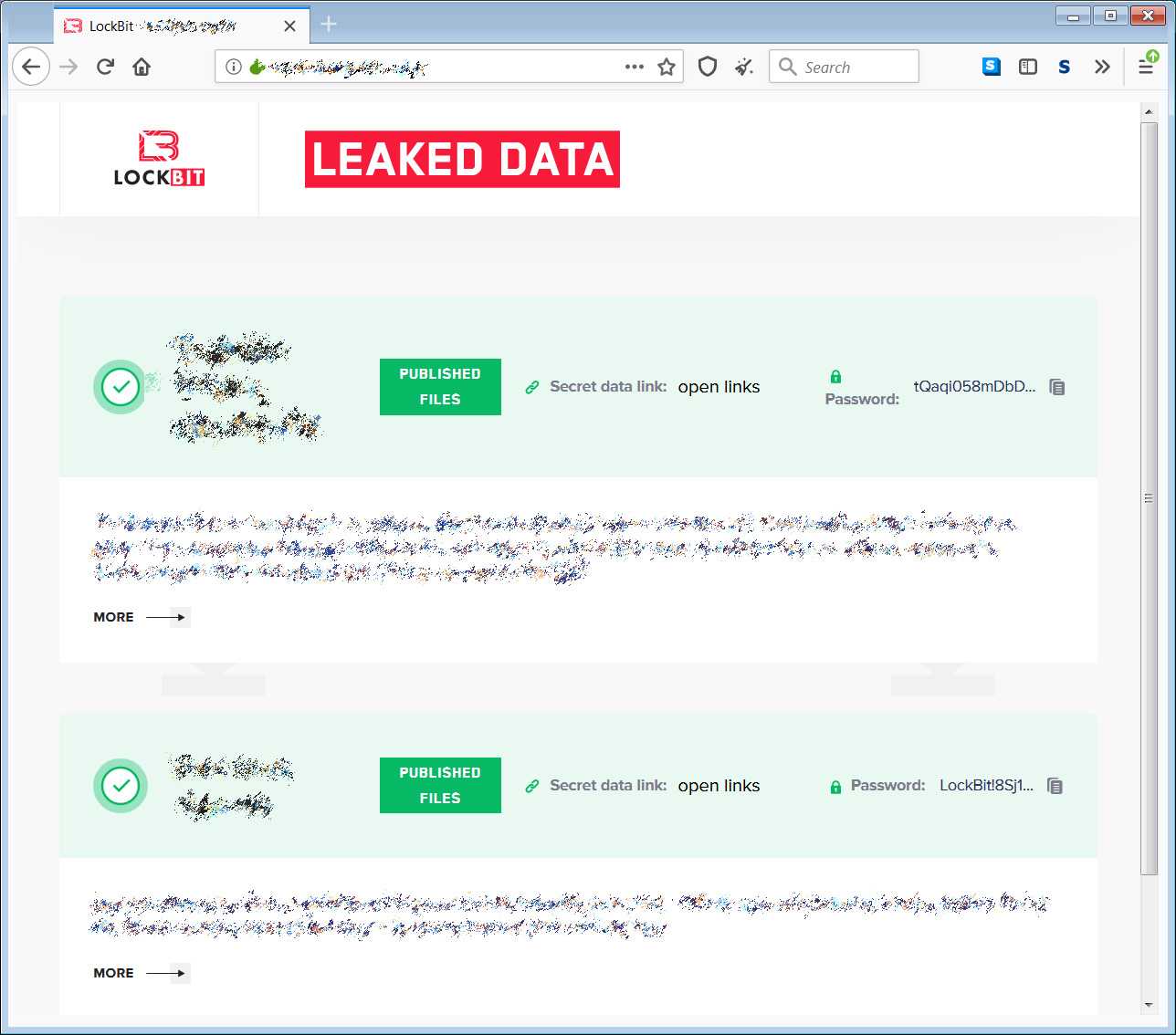
This peculiarity makes this malware very dangerous, especially because it targets very specific objectives: businesses or administrative organizations. Notable past goals include organizations in the United States, China, India, Indonesia, Ukraine. In addition, various countries across Europe (France, United Kingdom, Germany).
In fact, it seems that this control is carried out in an automated way, intentionally avoiding to attack certain systems. LockBit works like ransomware-as-a-service (RaaS), this means that anyone can rent their use by paying a deposit and the profits are split between the developers and the borrowers of the malware. This mode means that anyone, even without special technical knowledge, can enter this sort of affiliation circuit e by renting this “service”, can profit from it.
In fact, LockBit turns out to be a highly automated ransomware, once it enters the victim network, it only takes 5 minutes to activate the encryption routines on the target systems, bypassing the standard Windows protections, infecting and blocking a system after the ‘other.
LockBit: ransomware anatomy
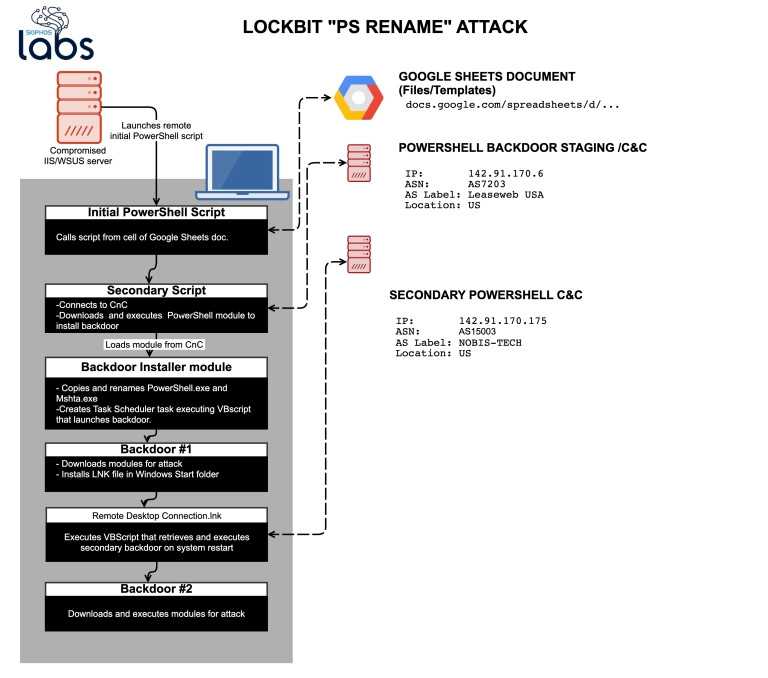
LockBit is a distributed malware: one part resides inside the victim machine and another part distributed on remote servers (Server C&C, command and control). The initial attack vector consists of a series of scripts in PowerShell, the first is used to download the second script.
The method used is quite particular: the second script it is contained within a cell of a Google Sheets file, in position B1 of the spreadsheet. The malware reads the content and transcribes it into a .ps file which becomes the second PowerShell script (everything is encoded in Base64).
The second script uses a System.Net.ServicePointManager object, which serves to provide management for HTTP connections, in fact it is used to connect to a server (142.91.170.6) to download another PowerShell script containing a BackDoor system and the piece of malware that connects to the C&C server.
The BackDoor uses Empire, a framework that offers encrypted communications and a series of tools used to evade detection by IPS and IDS devices, Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) that control and analyze all the activities of network, in order to find unusual data traffic.
Once the connection with the C&C server is established that download the necessary files for the BackDoor, it schedules the processes to ensure resilience on the victim system and launches a VBscript which executes the BackDoor.
The other modules that are downloaded are written in C #: one targets Microsoft’s antimalware system (AMSI), another verifies that the system is genuine and not a virtualized one for malware analysis, then checks the local registry of Windows looking for particular keywords that allow it to understand if it is a system containing valuable data, such as tax or banking data and if it finds what it was looking for it proceeds with the ramsonware operation otherwise it switches to another system, looking on the local network.
To spread LockBit makes ARP requests to find other active hosts on the network and once found it tries to connect to them tramite SMB (Protocol used on Microsoft networks for sharing files and folders).
LockBit: increasingly sophisticated ransomware, evolution
What makes LockBit an increasingly sophisticated ransomware is not only due to its evolution, but from how the authors have worked on the code to optimize it and make it more performing.
They have been detected three different versions del ransomware:
- Variant 1, abcd extension, initial version that renamed files with the .abcd extension and inserted the ransom note inside a text file that copies to each directory.
- Variant 2, LockBit extension, the file extension was changed to .LockBit, giving it its current nickname.
- Variant 3, LockBit version 2, it is with this version that we see the malware in its current form.
To make the ransomware even more sophisticated, the developers have written modules in C ++ with some additions made using Assembler. The binary makes use of Intel’s SSE instructions and specific features to boost its performance. One of the more advanced concepts applied in LockBit is the use of Input / Output Completion Ports (IOCP).
IOCPs are a model for advanced multi-thread management, that is, they allow processes to perform multiple I / O (input / output) operations simultaneously, making the data encryption phase much faster.
In a joint report by researchers at McAfee Labs and cybersecurity firm Northwave, which handled the response to the incident, it was found that LockBit managed to encrypt an entire corporate network in three hours by encrypting approximately 25 servers and 225 workstations.
How to protect yourself?
Let’s look at some of them below practical countermeasures to be taken to ensure adequate safety:
- Implementation strong passwords, many breaches occur due to password weakness.
- Enabling two-factor authentication discourages brute-force attacks and adds a higher level of security.
- Check the user account permissions, limiting the authorizations as much as possible and to the bare essential, especially on those stations that are more exposed.
- Delete the outdated user accounts and not used, they represent useless weak points to leave.
- Verify that system configurations follow all safety procedures, periodically evaluating the procedure operative standard in reference to new threats.
- Always have gods updated backups, especially in certain incidents, backup turns out to be our only lifeline.
- Provide systems with comprehensive antivirus solutions tailored to the system to be protected.