Kobalos is a small but complex malware that affects Linux-based supercomputers, but can also migrate to other operating systems
Researchers of ESET, a company specializing in cybersecurity known around the world, have recently discovered Kobalos, a malware that infects i supercomputer and in particular i cluster of high-performance computers known by the acronym of HPC. The company worked together with the cybersecurity team of the CERN and other organizations working within the landscape of prevention from attacks on scientific research networks. Among the victims, in fact, there seems to be an important Asian Internet Service Provider (ISP), a vendor dedicated to the security of North American endpoints and an unspecified number of private servers.
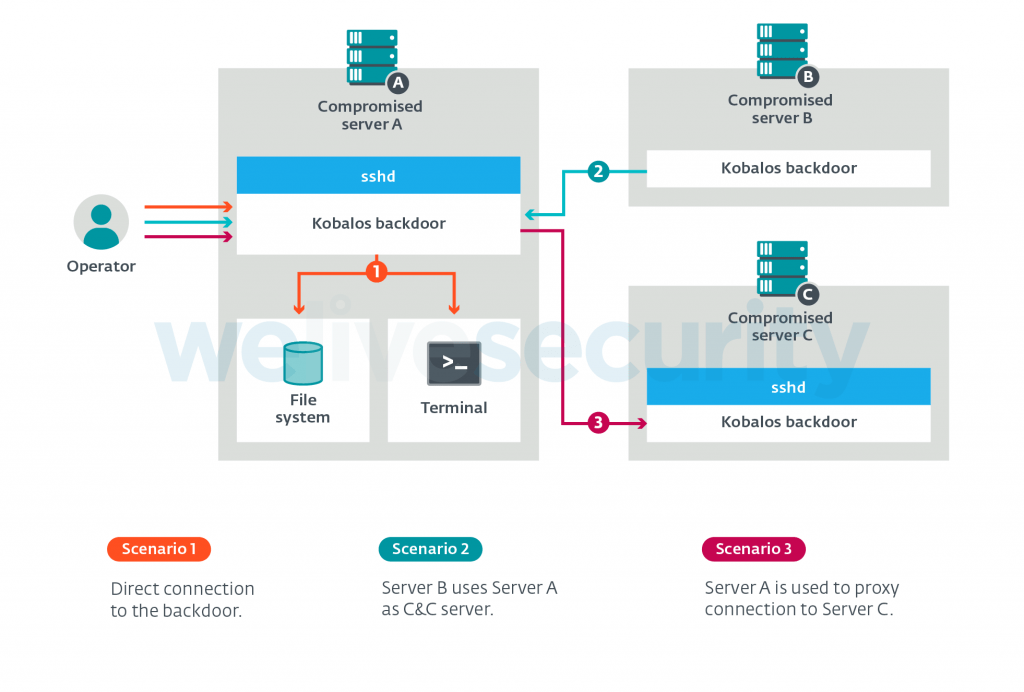
It is a small but complex piece of malware that can transfer itself via several operating systems including Linux, BSD, Solaris and certainly also AIX e Windows. The researchers decoded it with no small difficulty and Marc-Etienne Léveillé, a researcher who participated in the survey, explained:
“We called this malware Kobalos because of the tiny size of the code and its insidiousness; in Greek mythology, a Kobalos is a mischievous little creature. It must be said that such a level of sophistication is very rarely seen in Linux malware. Basically, Kobalos allows remote access to the file system, and gives the ability to generate terminal sessions and connect via proxy to other servers infected with this malware. “
Kobalos: a new threat for Linux and beyond
This, in a nutshell, means that any server that is compromised by Kobalos can be turned into a server Command&Control (C&C) by the hackers who infected him and all this through a single system command. Since the IP addresses and ports of the C&C server have fixed encodings in the executables, operators can generate more and more examples of Kobalos by exploiting the potential of the new C&C server that hosts it. Furthermore, most systems compromised by this malware have the client disabled for the SecureShell (SSH) and therefore can no longer secure system credentials.
Léveillé then concluded his analysis as follows:
“Anyone who uses an SSH server on an infected computer will have their credentials stolen. These can be used later by the attackers to install Kobalos on the server just hacked ”.
A tip to limit the functionality of the malware
One way to mitigate the functionality of the malware is configuration two-factor authentication for connecting to SSH servers because the use of stolen credentials seems to be one of the main methods of propagation of Kobalos.
What do you think of these results? Let us know in the comments and keep following us on the TechGameWorld.com pages where you can find the latest news and more.















