Sophos explains how it works and how you can defend yourself against Conti ransomware, one of the cyberthreats that has been infiltrating corporate networks for a year
Multinational leader in the latest generation of security, Sophos protects more than 400,000 companies of all sizes in over 150 countries from the most advanced cyber threats. Developed by SophosLabs – global research team – the cloud-native and AI-integrated security solutions protect endpoints, servers, mobile devices and networks from ever-evolving threats, including automated breaches, ransomware, malware, exploits, data theft, phishing, and more.
Precisely because of their capacity, the Sophos Rapid Response was called to analyze, neutralize and face the ransomware “human-operated” Conti. This attack develops in 5 days from the moment of the initial compromise to the restoration of business operations. The perpetrators of this attack threaten their victims, after having stolen sensitive data and encrypted them, to make them visible on the “Conti News” site if the ransom is not paid. Let’s find out what to do in case of an attack and how to defend ourselves against Conti ransomware.
Here is Sophos’s study of Conti ransomware
The three-part report released by Sophos, “The Realities of Conti Ransomware“, is formed from:
- A ransomware attack Conti day by day – Analysis of Accounts attack methodology, including indicators of compromise (ioC) and tactics, techniques and procedures (TTPs)
- Accounts Ransomware: Evasive by nature – A technical overview of Conti’s evasive nature by Sophos researchers
- What to expect if you get hit with the Conti ransomware – A set of tips that provide IT managers facing the trumpact of an Conti attack with useful information on what to do in a timely manner and a 12-point checklist to help them investigate the attack. the checklist guides IT administrators through everything Conti attackers might do while inside the network and the major TTPs they are likely to use.
Peter Mackenzie, manager di Sophos Rapid Response, explained the following:
In cases of human-operated attacks, those leading the offensive can adapt and react to changes in real time. In this case, access to two servers was gained at the same time, so when the victim detected the attack and disabled one of them (convinced that they had blocked the ransomware), the cybercriminals had to do nothing but switch to the attack. other server and continue your attack undisturbed. Having a plan B is a common approach to human-operated attacks and is an important reminder that blocking suspicious activity on your network doesn’t mean the attack is over.
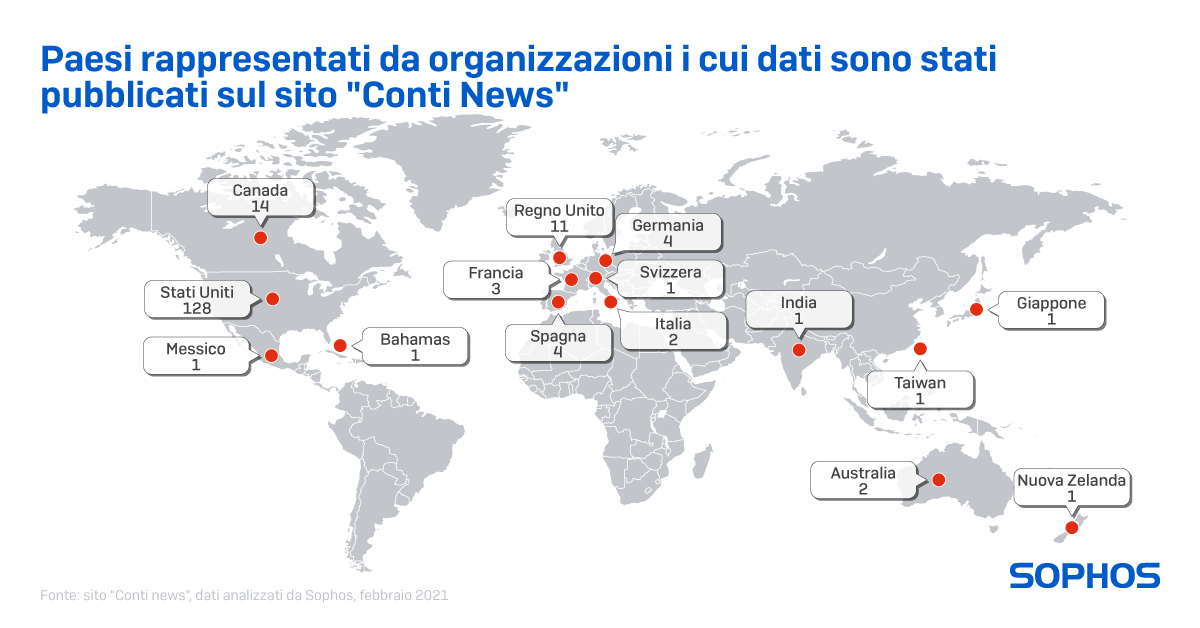
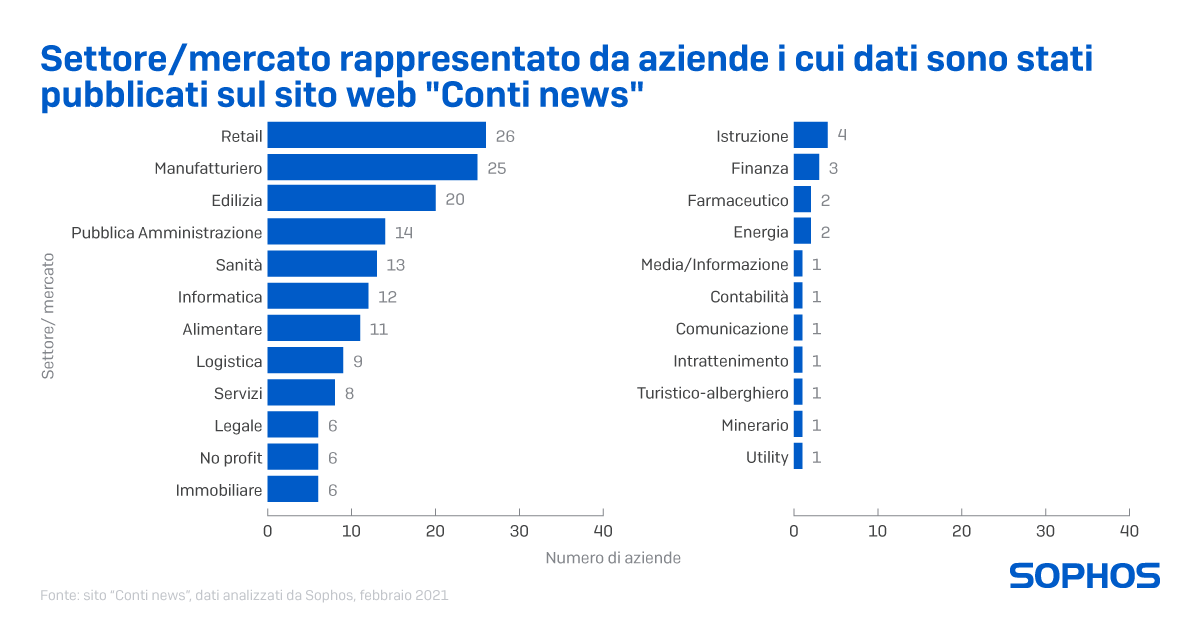
The site “Conti News” has published to date the data stolen from 180 victims; Sophos created a profile of the victims based on this data (which covers approximately 150 companies whose data was published at the time of the analysis). Here is the list of actions that will help IT managers cope with the hours and days following the attack.
What to do in case of attack
- Close any Internet-connected Remote Desktop Protocol.
- If RDP access is required, set it up behind a VPN connection.
- Use multi-layered security to prevent, protect and detect cyberattacks. This will have to include EDR systems and Managed Threat Response teams to monitor the corporate network 24 hours a day, 7 days a week without interruptions.
- Be aware of the five signs that the company is about to be attacked in order to act promptly and stop the attack.
- Have an effective incident response plan and update it when necessary. If the company does not have the specific resources or skills to manage these aspects, it is advisable to contact experts for further support and advice. If you do not feel confident that you have the skills or resources to do this, to monitor threats or to respond to emergency incidents, it is recommended that you turn to outside experts for help.
This will block Conti ransomware and associated files. While it’s not a walk in the park, at least a method has been found to counter these ongoing threats. Having your computer hacked, especially for a company, is never a good thing. To understand how hackers can act, I invite you to read the Cisco Talos interview to one of them. To read it you can click here. Did you know about this ransomware? Have you ever had anything to do with it? Let us know yours in the comments. In order not to miss further news from the software universe, keep following the pages of tuttooteK!















